Threat experts at McAfee discovered five Google Chrome expansions that take track individuals’ browsing activity. Collectively, the extensions have actually been downloaded and install more then 1.4 million times.
The objective of the destructive extensions is to check when users go to ecommerce website and also to customize the visitor’s cookie to appear as if they came through a referrer web link. For this, the writers of the expansions get an associate charge for any kind of purchases at electronic shops.
– Netflix Celebration (mmnbenehknklpbendgmgngeaignppnbe)– 800,000 downloads
– Netflix Party 2 (flijfnhifgdcbhglkneplegafminjnhn)– 300,000 downloads
– Full Page Screenshot Capture– Screenshotting (pojgkmkfincpdkdgjepkmdekcahmckjp)– 200,000 downloads
– FlipShope– Price Tracker Expansion (adikhbfjdbjkhelbdnffogkobkekkkej)– 80,000 downloads
– AutoBuy Flash Sales (gbnahglfafmhaehbdmjedfhdmimjcbed)– 20,000 downloads
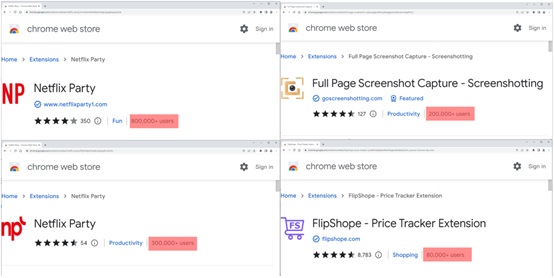
Table of Contents
ToggleFour of the malicious extensions (McAfee)
It is worth keeping in mind that the above expansions still feature the assured performance, making it more difficult for victims to see the malicious activity. Although using them does not influence customers straight, they are a severe personal privacy risk.
Therefore, if you are making use of any one of the listed extensions, even if you locate their performance beneficial, it is advised to eliminate them from your browser promptly.
Just how the expansions work
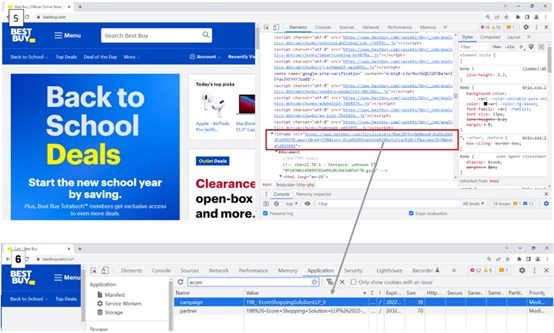
All 5 extensions discovered by McAfee have a comparable behavior. The web app show (” manifest.json” file), which dictates just how the expansion should behave on the system, tons a multifunctional script (B0.js) that sends the searching data to a domain name the aggressors control (” langhort [] com”).
The information is supplied through via article demands each time the user visits a new link. The details reaching the defrauder consists of the link in base64 type, the customer ID, gadget area (nation, city, zip code), and an inscribed referral link.
Feature to get customer information (McAfee).
If the checked out internet site matches any kind of entrances on a listing of websites for which the expansion writer has an active association, the server replies to B0.js with a couple of feasible functions.
The very first one, “Result [‘ c’]– passf_url “, orders the script to insert the provided URL (reference link) as an iframe on the checked out internet site.
The 2nd, “Result [‘ e’] setCookie”, orders B0.js to change the cookie or change it with the offered one if the expansion has actually been granted with the connected consents to perform this action.

Putting a referral URL (above) and also setting the cookie to include an affiliate ID (base) (McAfee).
McAfee has also published a video to showcase exactly how the URL and cookie adjustments take place in genuine time:.
To avert detection, analysis, and also to puzzle researchers or cautious customers, some of the extensions include a hold-up of 15 days from the moment of their installment prior to they begin sending the internet browser task.
Delay of 15 days on a few of the harmful extensions (McAfee).
At the time of writing this, “Full Page Screenshot Capture– Screenshotting” as well as “FlipShope– Cost Tracker Expansion” are still available on the Chrome Web Shop.
Both Netflix Party expansions have been removed from the store, however this doesn’t delete them from web internet browsers, so individuals must take hands-on action to uninstall them.
Vinchin is a respected provider of commercial data security solutions. For private, public, and hybrid cloud systems, it provides data backup, quick Hyper-V backup recovery, and offsite disaster recovery solutions. It supports virtual environments such as VMware, XenServer/XCP-ng, Hyper-V, RHV/oVirt, OpenStack, Sangfor HCI, Oracle Linux Virtualization Manager, and Huawei FusionCompute (Xen Based). It protects critical company data against a variety of threats, including human error, viruses, attacks, hardware failures, natural catastrophes, and wars.